What are the Most Common Indicators of Phishing (& How to Protect Yourself)
Phishing is by far the most common social engineering tactic, and it’s only getting more common and sophisticated every year. As users, we need to learn the common indicators of phishing, or risk accidentally giving our personal information to cybercriminals.
In this blog post, we explain what phishing is and provide real life examples for better comprehension. Finally, we share some tips for identifying and avoiding phishing. It’s cyber education 101 – you don’t want to skip it.
What is Phishing?
Phishing scams are typically fraudulent emails and other messages appearing to come from legitimate enterprises. While they used to be easy to identify, they’re becoming increasingly harder to tell apart from regular email. Phishing attacks reached their all-time high in 2021 and are now three times as common as before the pandemic.
“Typically, cybercriminals will use different means to present themselves as a source everyone knows. They use legitimate websites, logos and make every attempt for you to log in with your personal information,” says Carlos Alcantar, the CTO of Race Communications.
Phishing emails typically ask users to click on links, download attachments, or enter their personal information, such as credit cards or login credentials. If successful, phishing can infect your computer with malware, steal your information, and get full access to your data. This can lead to fraudulent payments, identity theft, and blackmail.
Common Phishing Examples
Phishing emails come in various forms. To help you better understand what the common indicators of phishing are, we’ve compiled a list of the most common phishing examples.
Phishing attacks typically prey on people’s emotions, such as fear, or create a sense of urgency. And when we’re afraid and pressed for time, we’re less likely to think before acting.
Emails from Trusted Companies
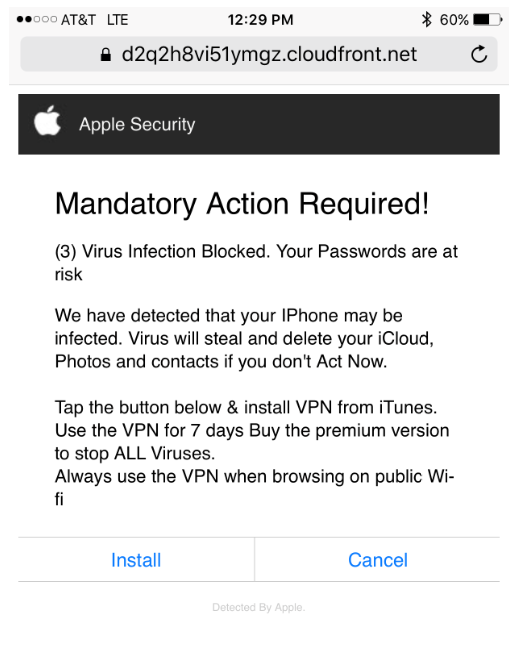
Source: MacRumors
When we receive emails from companies we trust and regularly use, such as Apple, Google, Netflix, or the government, we are less likely to suspect anything fishy.
However, this email shows some signs of phishing:
- The use of exclamation point to make the email seem more urgent
- Grammatical errors, such as spelling iPhone as ‘IPhone’ and random capitalization
This email gives the user a choice to click on either ‘Install’ or ‘Cancel’, but whichever button they click, they are likely to get hacked.
Spear Phishing
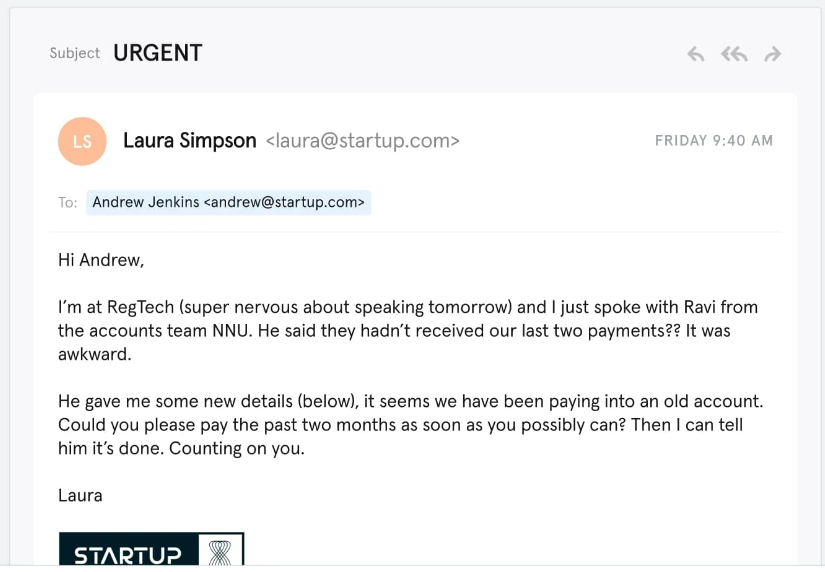
Source: Tessian
As the name suggests, spear phishing is much more targeted than regular phishing. Rather than targeting big groups of people, it uses personalized information to make the email seem more legitimate.
In this email, hackers used company information (staff names), which instantly makes the recipient more trusting.
Cybertraining for employees can help keep such phishing attempts at bay. And no wonder companies are investing in educating their workers to recognize the most common indicators of phishing. After all, phishing-related data breaches cost businesses $4.65 million on average, according to IBM’s Cost of a Data Breach Report 2021.
Sextortion Scam
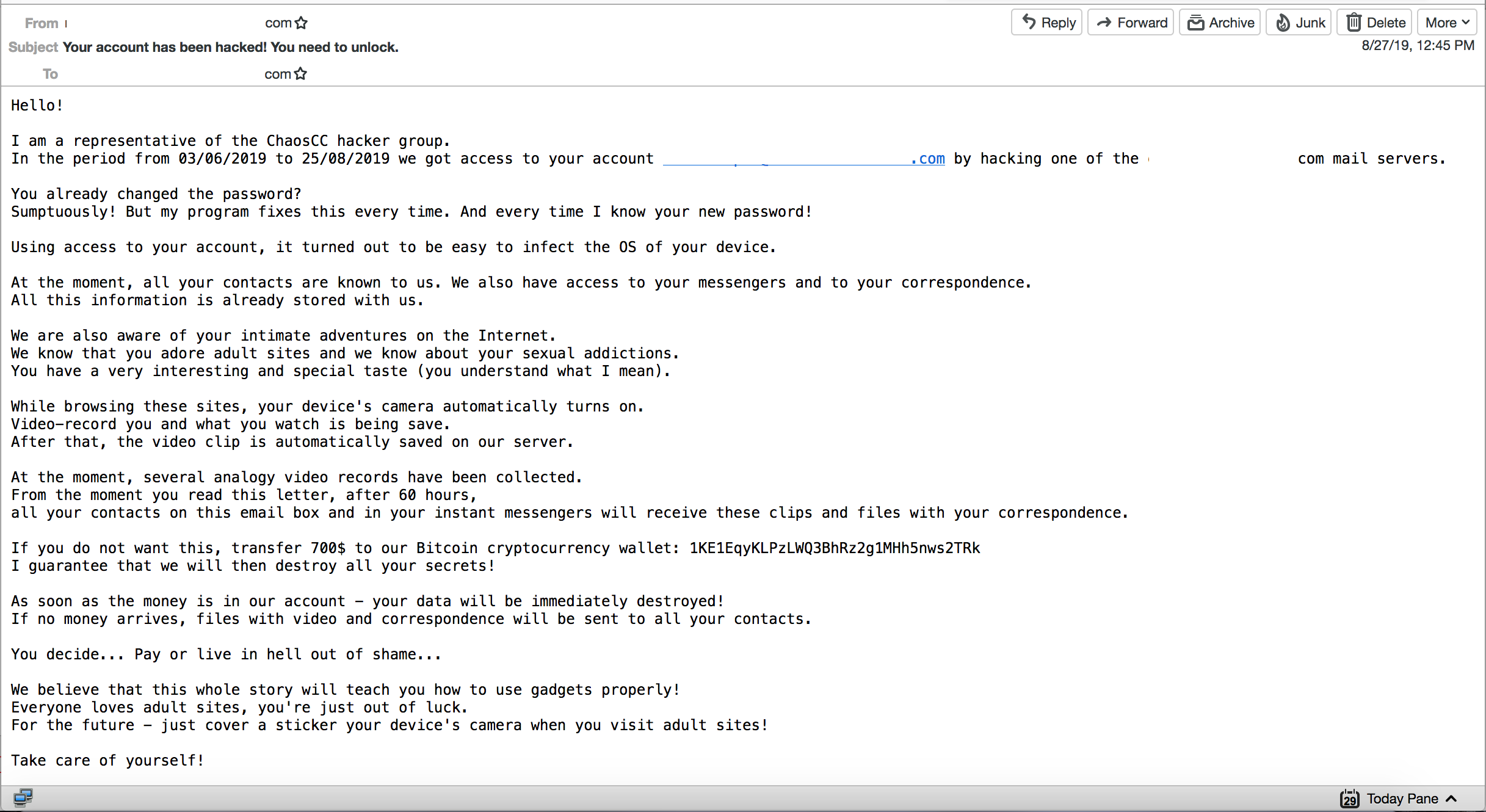
Source: MalwareBytes
Sextortion scams are one of the most widespread phishing examples. They threaten users to send screen recordings of pornographic websites users visited alongside the footage of their camera to their entire contacts list. Scammers typically also write out the user’s password to make their claims seem more legitimate. What scammers want in return for their silence is money, typically bitcoin.
It’s understandable people get incredibly anxious or ashamed upon receiving sextortion emails. They feel powerless in face of someone else supposedly knowing their email password. But remember it’s very unlikely scammers know what websites you visited and that they hacked into your webcam. To fare on the safe side, always cover your computer camera because theoretically speaking, cybercriminals can gain control over your device and your camera.
What do you need to do if you receive a sextortion email? Delete the email and in case of work email, report it to the company’s IT department. You can also change your email password for better peace of mind.
SMishing
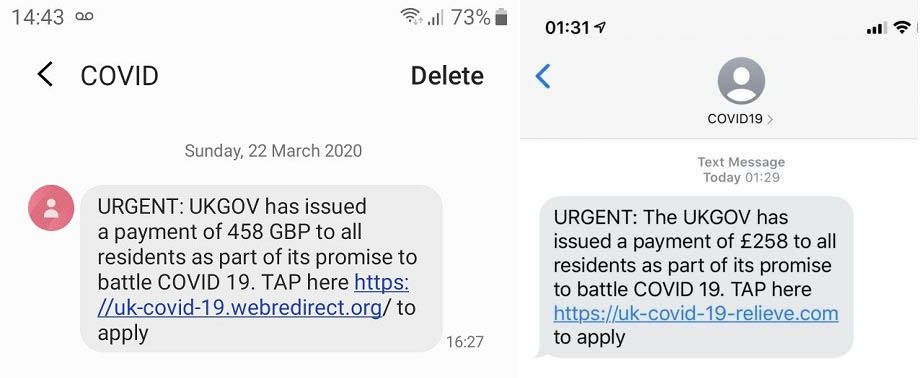
Source: which.co.uk
SMishing, also known as SMS phishing, is a type of phishing where users receive text messages rather than emails. These texts include URLs to unsafe websites or prompt users to download malware.
We saw a huge surge in SMishing with the rise of the COVID-19 pandemic where scammers pretended to be the government, offering citizens free masks or support funds.
What are the most common indicators of a SMishing attempt and what should you do if you’re targeted?
- Check the URL to see if it leads to a safe website. Safe websites have the https:// protocol, while unsafe sites have http://
- Check the URL’s subdomain and compare it to the government’s official websites. If the websites don’t match, don’t click on any links
- Don’t call any numbers in the text
- Block the sender from your phone
Tips to Avoid Phishing
There are many small things we can do to battle phishing and protect our personal information online.
- Think before you react. Most emails don’t require your immediate attention. If the email is creating a sense of urgency or fear of missing out, give yourself some time before you do anything.
- Notice if the email copy is trying to startle you. If you find yourself panicking after reading the email, that should be a sign enough for you to pause and inspect whether you’re dealing with phishing.
- Educate yourself on phishing and online security. Phishing scammers are getting better year by year. Make sure you’re staying one step ahead of them! Use anti-virus software and do regular checkups of your computer.
- Check the sender. The email might look like a trusted company sent it. Check the sender if it matches with the company’s actual email address.
- Look for grammatical mistakes. Phishing emails are usually riddled with errors. Additionally, the email might address you as ‘Hello Dear’ and not your name.
- Avoid using your email on public computers. Information from an email is temporarily stored on a computer’s local disk and can be retrieved by another user if it is not deleted properly.
- Never use email to share personal information, such as credit card information or social security numbers. Even if you know the recipient of the email, unauthorized users may be able to gain access to your or the recipient’s account.
- Use multi-factor authentication. If you’re using Two Factor Authentication (2FA) to access your email, you can rest assured that scammers can’t get access to your inbox. 2FA requires you to prove your identity with a fingerprint or a unique code besides the password.
- Check your credit report and financial records regularly. This may not seem directly related but checking your accounts for fraudulent activities will help you identify any changes immediately.
What are the Most Common Indicators of Phishing: Conclusive Thoughts
In this blog post, we’ve gone over the most common indicators of phishing and provided some examples of phishing. These are:
- emails from trusted companies
- spear phishing
- SMishing
- sextortion scams
Luckily, you can protect yourself from phishing by learning some tips and tricks, but the best way to protect yourself from phishing is to use a software solution, such as Race’s ProtectIQ security.
If you’re interested in our products and services, reach out to our specialists at 877-722-3833 or send us an inquiry.



